Table of contents
- Why Governance Matters
- Azure Blueprints: The Blueprint for Governance
- Microsoft Defender: Your First Line of Defense
- Building a Governance Framework: The Technical Details
- Real-World Scenario: Putting Governance into Practice
- Pros and Cons: The Good, the Bad, and the Azure
- Additional Resources: Where to Learn More
- Visuals: A Picture is Worth a Thousand Policies
- Summary
As organizations increasingly adopt Azure, it's important to have a governance framework in place to manage and secure the cloud environment. A governance framework helps to ensure compliance, improve security, and optimize resources. In this article, we will explore the best practices and techniques for building a governance framework for Azure.
Why Governance Matters
Before diving into the technical details of building a governance framework, let's first understand why governance matters. Governance is like the "parent" of your Azure environment, making sure that everything is running smoothly and that there are no rogue "cloud teenagers" causing chaos.
In a more serious tone, Governance helps to ensure compliance with industry standards and regulations, improve security, and optimize resources. Without a governance framework, your Azure environment could become a wild west of uncontrolled and unsecured resources.
Azure Blueprints: The Blueprint for Governance
Azure Blueprints is a service that allows you to create, manage, and share a collection of Azure resources, policies, and RBAC roles that define a compliant environment. Azure Blueprints enables you to define a repeatable set of Azure resources and configurations, and then quickly and consistently deploy them across subscriptions and management groups.
For example, you can use Azure Blueprints to create a blueprint for a compliant environment that includes a specific set of Azure policies, RBAC roles, and resources. You can then assign this blueprint to multiple subscriptions or management groups, ensuring that they all have the same set of compliant resources and configurations.
Here is an example of how to create an Azure Blueprint using Azure CLI:
az blueprint create --name "MyBlueprint" --definition "https://raw.githubusercontent.com/Azure/blueprints/master/blueprint-samples/compliance/compliance-blueprint.json" --subscription "MySubscription"
Microsoft Defender: Your First Line of Defense
Microsoft Defender is a security service that provides real-time protection for Azure resources. Microsoft Defender uses advanced threat protection, behavioral analytics, and machine learning to detect and respond to threats.
For example, you can use Microsoft Defender to detect and respond to malicious activity on your Azure resources, such as a compromised virtual machine or a malicious file uploaded to a storage account. You can also use Microsoft Defender to integrate with Azure Policy and Azure RBAC to enforce security policies and limit access to resources.
Here is an example of how to enable Microsoft Defender for Azure Storage using Azure CLI:
az storage account update --name <storage-account-name> --resource-group <resource-group-name> --enable-azure-files-aad
By including Azure Blueprints and Microsoft Defender in your governance framework, you can ensure that your Azure environment is compliant, secure, and well-managed.
Building a Governance Framework: The Technical Details
Building a governance framework for Azure involves several technical components such as Azure Policy, Azure Role-Based Access Control (RBAC), and Azure Locks.
Azure Policy is a service that allows you to create, assign, and manage policies that enforce rules and effects for your resources. For example, you can use Azure Policy to ensure that all virtual machines are running the latest version of the operating system or that all storage accounts are encrypted. Here is an example of an Azure Policy definition that enforces that all virtual machines have Azure Security Center enabled:
{
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Compute/virtualMachines"
},
{
"field": "Microsoft.Compute/virtualMachines/securityProfile.enableSecurityCenter",
"equals": false
}
]
},
"then": {
"effect": "deny"
}
}
Azure RBAC is a service that allows you to manage access to Azure resources. For example, you can use Azure RBAC to grant certain users or groups access to specific resources or to limit the actions that they can perform on those resources. Here is an example of how to assign a role to a user using Azure CLI:
az role assignment create --assignee <user-email> --role <role-name> --scope <resource-id>
Azure Locks is a service that allows you to prevent accidental deletion or modification of resources. For example, you can use Azure Locks to prevent a virtual machine from being deleted or modified. Here is an example of how to create a lock on a resource using Azure CLI:
az lock create --name <lock-name> --resource-group <resource-group-name> --resource-type <resource-type> --resource-name <resource-name> --lock-type <lock-type>
You can use Azure Policy, Azure RBAC, and Azure Locks together to create a governance framework that helps to ensure compliance, improve security, and optimize resources.
Real-World Scenario: Putting Governance into Practice
Now that we've covered the technical details of building a governance framework, let's take a look at a real-world scenario where a governance framework can be applied.
One real-world scenario where Azure Blueprints and Microsoft Defender can be particularly useful is in the healthcare industry, where compliance with regulations such as HIPAA is critical. A healthcare organization can use Azure Blueprints to create a blueprint for a compliant environment that includes Azure policies for data encryption, Azure RBAC roles for access control, and specific Azure resources such as virtual machines. They can then assign this blueprint to multiple subscriptions or management groups, ensuring that all resources are deployed consistently and compliantly.
Microsoft Defender can be used to monitor and protect these resources from threats. The organization can enable Microsoft Defender for Azure Storage, to detect and respond to malicious activity on their storage accounts. They can also use Microsoft Defender to integrate with Azure Policy and Azure RBAC to enforce security policies and limit access to resources, such as only allowing access to specific virtual machines for authorized personnel. This way, the organization can ensure compliance with HIPAA regulations while improving security and monitoring the resources.
By using Azure Blueprints and Microsoft Defender together, healthcare organizations can ensure that their Azure environment is compliant with regulations such as HIPAA and secure from potential threats, while also optimizing resources.
Pros and Cons: The Good, the Bad, and the Azure
Building a governance framework for Azure is not without its drawbacks, so let's take a look at the pros and cons of building a governance framework.
Pros:
Ensures compliance with industry standards and regulations
Improves security
Optimizes resources
Can prevent costly mistakes
Cons:
Can be time-consuming and complex to set up
Can be challenging to maintain
Can be restrictive for users
Additional Resources: Where to Learn More
Building a governance framework for Azure is a complex task, and there's always more to learn. Here are some additional resources to help you learn more about governance on Azure:
Visuals: A Picture is Worth a Thousand Policies
Building a governance framework for Azure can be complex and abstract, and sometimes a picture is worth a thousand policies.
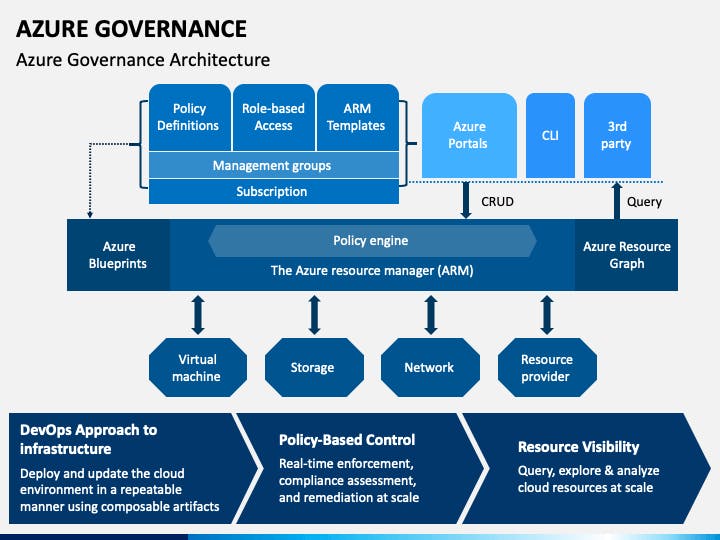
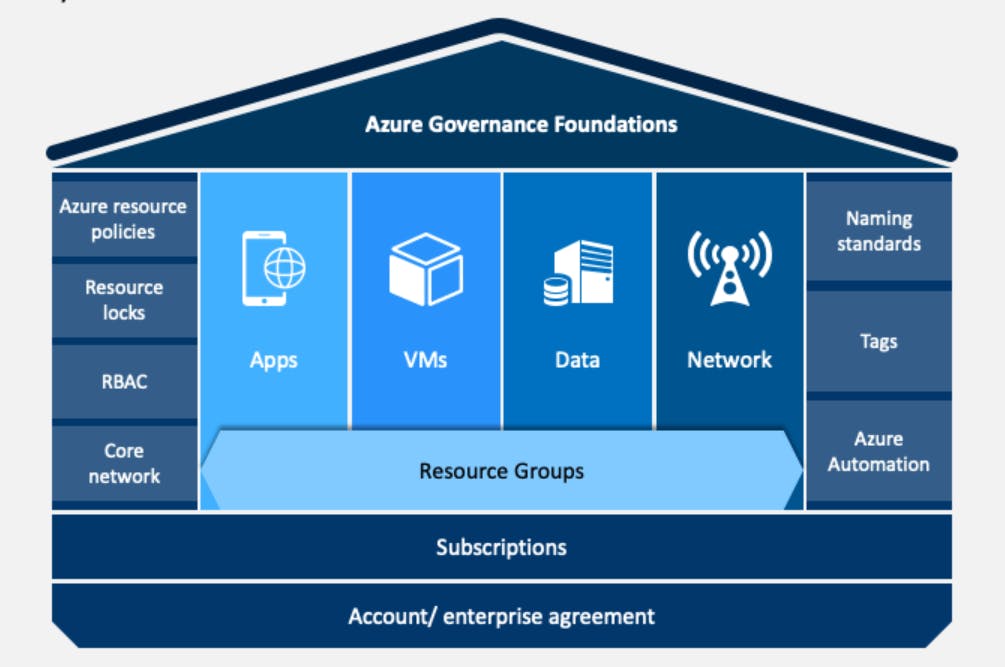
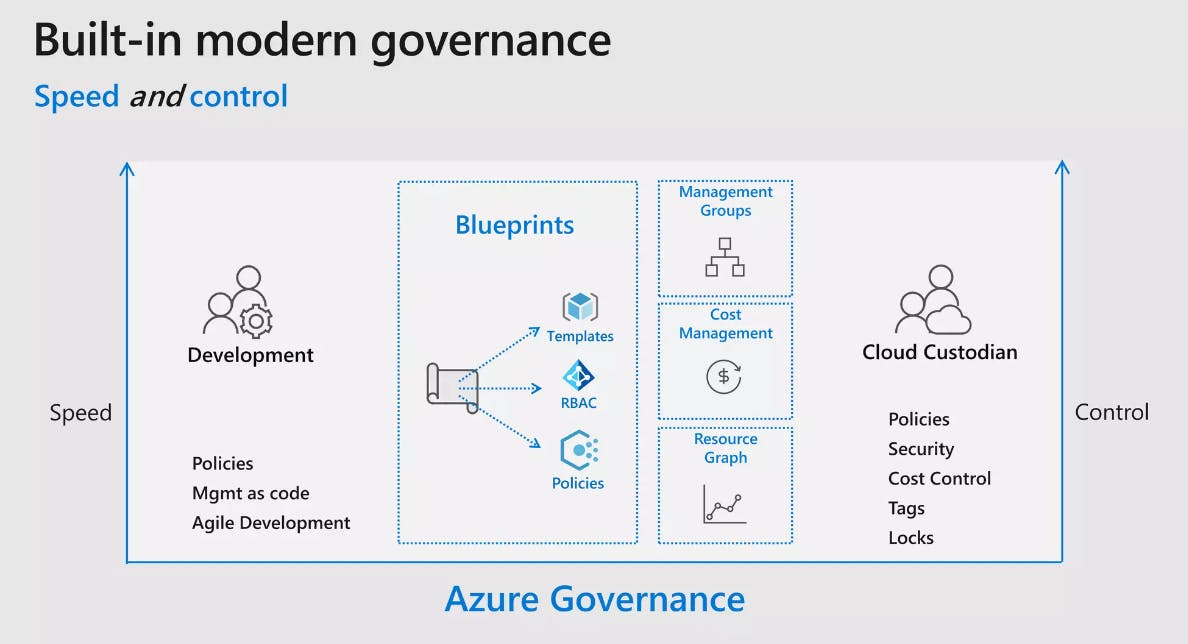
Summary
In conclusion, building a governance framework for Azure is an important task that can help ensure compliance, improve security, and optimize resources. By utilizing Azure Blueprints, Microsoft Defender, Azure Policy, Azure Role-Based Access Control (RBAC), and Azure Locks you can create a comprehensive governance framework that will help you manage your Azure environment effectively. Remember that it's important to understand the real-world scenarios and the pros and cons of each service and how to use them. With the right governance framework in place, you can ensure that your Azure environment is secure, compliant, and well-managed.

